Cyber Security Detection
Posted by Weisheng Zhong
Attacks on computer infrastructures are becoming an increasingly serious problem. Cyber attacks are actions that attempt to bypass security mechanisms of computer systems. A cyber attack would cause loss of integrity, confidentiality, denial of resources. Attacks are wide-ranging, global and do not seem to discriminate among governments and companies.
Cyber attack detection is based on assumption that intrusive activities are noticeably different from normal system activities and thus detectable. Cyber attack detection has been defined as “the problem of identifying individuals who are using a computer system without authorization and those who have legitimate access to the system but are abusing their privileges.
In this blog post we’ll firstly introduce main types of cyber attack. Additionally, we'll present some research work related to cyber attack detection.
Types of Cyber Attack
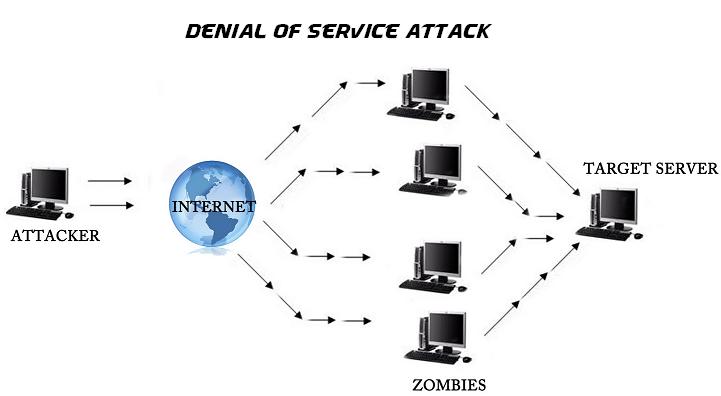
1. Denial of Service Attacks: Denial of service (DOS) is class of attack where an attacker makes a computing or memory resource too busy or too full to handle legitimate requests, thus denying legitimate user access to a machine. There are two general forms of DoS attacks: those that crash services and those that flood services. The most serious attacks are distributed.
2. Remote to Local (User) Attacks: A remote to local (R2L) attack is a class of attacks where an attacker sends packets to a machine over network, then exploits the machine’s vulnerability to illegally gain local access to a machine. It occurs when an attacker who has the ability to send packets to a machine over a network but who does not have an account on that machine exploits some vulnerability to gain local access as a user of that machine.
3. User to Root Attacks: User to Root (U2R) attacks are exploitations in which the hacker starts off on the system with a normal user account and attempts to abuse vulnerabilities in the system in order to gain super user privileges. The U2R attacks lead to several vulnerabilities such as sniffing password, a dictionary attack and social engineering attacks.
4. Probing: Probing is an attack in which the hacker scans a machine or a networking device in order to determine weaknesses or vulnerabilities that may later be exploited so as to compromise the system. This technique is commonly used in data mining, e.g. mscan, nmap and etc.
Genetic Algorithm based Approach
In this paper, an idea for use of a Genetic Algorithm (GA) based approach for generation of rules to detect Probing, DoS and R2L attacks on the system is proposed. Genetic Algorithm (GA) is based on the Darwin‟s theory of evolution; the basic rule is” Survival of the fittest”. GA handles a population of possible solutions. Each solution is represented through a chromosome. GA uses an evolution and natural selection that uses a Chromosome-like data structure and evolve the chromosomes using selection, recombination(crossover) and mutation operators. An evaluation function called "Fitness Function" is used to calculate the goodness of each chromosome according to the desired solution. During the process of evaluation “Crossover” is used to simulate natural reproduction and “Mutation” is used to mutation of species. For survival and combination the selection of chromosomes is biased towards the fittest chromosomes.

The system architecture contains two stages. Within the initial one, the learning stage, using network audit data to generated rule set for detecting intruders. The second stage, highest fitness value and best rule set is used for detect intruders in the internet globe. Genetic Algorithm works on an individual called chromosome and evolves the group of chromosomes to a population of quality individuals. Each chromosome represents a technique to solve the problem. A fitness function is a measure of each rules implementation. A group of suitable chromosomes are selected using a fitness function initially eliminating the other individuals. The sub attack labels (smurf, mailbomb, saint, warezmaster etc.,) are recognized with respect to the fitness criteria by selecting the best-fit chromosomes capable of detecting the attacks from every population.
Agent based Approach
In this approach, servers can communicate with one another and can alarm each other. In order to respond to an attack, sometimes it can be sufficient enough to disconnect a subnet. In this type of system in order to contain a threat, the distributed Computerized Attack/Defense System (CADS) can order severs, routers or network switches to disconnect a host or a subnet. There are two approaches in implementing an agent based technology. In the first approach, autonomous distributed agents are used to both monitor the system and communicate with other agents in the network. In the second approach, a multi-type agent based system is proposed, where each one of these agents performs a different task and has its own subcategories.

Hidden Markov Models (HMM) based approach
Sung-Bae Cho
presents a novel intrusion detection system (IDS) that models normal behaviors with hidden Markov models and attempts to detect intrusions by noting significant deviations from the models. Among several soft computing techniques neural network and fuzzy logic are incorporated into the system to achieve robustness and flexibility. Self-organizing map (SOM) determines the optimal measures of audit data and reduces them into appropriate size for efficient modeling by HMM. In this paper, three models based on HMM with different measures are implemented. The problem is to decide if the present behavior is abnormal from the three information sources that are inherently imprecise and uncertain. Fuzzy logic is used to make the final decision of whether current behavior is abnormal or not from the three sources of information to improve the performance and reliability of the system.

IDS in Cloud
Providing security in a distributed system requires more than user authentication with passwords or digital certificates and confidentiality in data transmission. Distributed model of cloud makes it vulnerable and prone to sophisticated distributed intrusion attacks like Distributed Denial of Service (DDOS) attacks. To handle large scale network access traffic and administrative control of data and application in cloud, a new multi-threaded distributed cloud IDS model has been proposed by Shelke et. al
. The proposed cloud IDS handles large flow of data packets, analyze them and generate reports efficiently by integrating knowledge and behavior analysis to detect intrusions. A multi-threaded IDS would be able to process large amount of data and could reduce the packet loss. After an efficient processing the proposed IDS would pass the monitored alerts to a third party monitoring service, who would in turn directly inform the cloud user about their system under attack. The third party monitoring service would also provide expert advice to cloud service provider for mis-configurations and intrusion loop holes in the system.

Discussion
Tradiational cyber attacks detection methods have limiations. The main limiation of is that they only could detect pre-known attacks accurately. They might fail to recognize novel or unseen cyber attakcs.
Instead of focusing on cyber attacks detection inside computer systems or networks, I have more interest on how to detect a cyber attack in real-time and how to evaluate the impact of a detected attack. Nowadays social media becomes a powerful tool to collect social opinions since people would like to share their feelings and moments using social media tools, like Twitter and Facebook. And recently some cyber attack events have a huge impact on people's life, for example, Yahoo user accounts hacking event in 2012 and the WannaCry ransomware attack in 2017. People who got involved with these attacks would like to post related information on social media, so I think we can use these information to perform early detection of cyber attacks, before offical accounts, websites or media conform these attack events are true.