As you may know, radio frequency is the most valuable resource in wireless communications. With the rapidly growing demand of frequency spectrum hungry devices and applications, regulators such as the Federal Communication Committee (FCC) are working with private sectors on novel spectrum sharing technologies. Specifically, the FCC recently finalized its ruling on Citizens Broadband Radio Service (CBRS) which opens 3550-3700 MHz band (aka. 3.5 GHz Band) for public use [2]. This gives a huge incetive for the development of applications of 3.5 GHz band and also raises many more problems to deal with. One of the most discussed issues is privacy of primary users, whose private information such as locations, time of operation, frequency of operation may be breached when they have to share a same spectrum band with the public, to whom the adversaries often belong. This blog will address on the privacy of the most sentive information of primary users - location. We will check out the three tiers of users and the spectrum access system, the location privacy problem, and how two research papers dealt with this problem.
Users and Spectrum Access System in 3.5 GHz Band
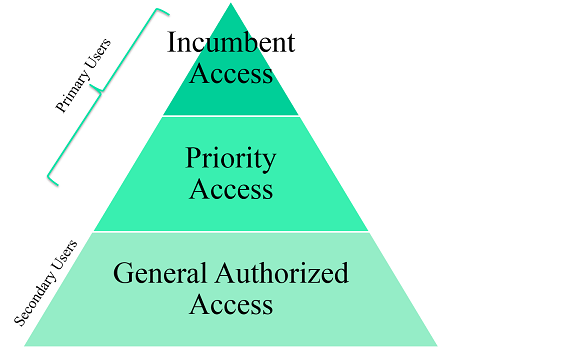
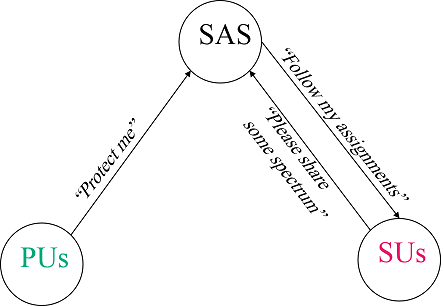
Figure 1. Three tiers of spectrum users. Figure 2. Conceptual SAS operations.
There are three types of users allowed in CBRS shown in Figure 1:
- Incumbent Access Users: Federal radars, FSS earth stations, Grandfathered satellite services users, and other registered non-federal incumbents.
- Priority Users: Users with Priority Licenses (PAL) that will be assigned by competitve bidding.
- General Authorized Access Users: Users with flexible access to unused PAL channels.
In research communities, the first two tiers of users are referred as "Primary Users" and the third tier of users are referred as "Secondary Users". We will use "PU" and "SU" for convenience. The Spectrum Access System (SAS) is the central scheduler that assigns unused spectrum to SUs by request, as shown in Figure 2. The SAS collects information from PUs, deals with SU requests with the caution of preserving PU's private information. Usually the SAS is equipped with a Geolocation Database (GDB) to store both PU and SU locations and compute the optimal spectrum assignments for SUs' queries.
We will focus on the model proposed by [4], which gives a mathematical model on the data flow between SAS with PUs and SUs, shown in Figure 3.

Figure 3. SAS data flow model.
The parameters of this above model is shown in Table 1:
Table 1. SAS model parameters.

As a short summary of this data flow model, the PUs first register their characteristics such as locations, intereference threshold and requirements to the SAS database. During operation, an SU sends a spectrum request along with its location, channel gain, and profitable transmission power to the SAS. The SAS solves an optimization problem that maximizes SU's utility of the sprectrum while guranteeing the PUs' intereference requirements. As a note, the PUs' interference requirement does not provide a solution to their location privacy. We will delve into the privacy issue in the following sections.
Inference Attacks against PU Location Privacy
After the introduction of the system model and math definitions, we can finally come to the privacy problem. The privacy problem of general multi-user spectrum sharing system was first mentioned in [6], which mainly considers protecting military spectrum users. The attacks on PUs' location privacy with statistical inference was first formalized in [3]. Here we assume the communications between the PUs and the SAS is absolutely safe, the adversary usually hacks several SUs or an entire SU network so that it can fetch information through request-response with the SAS. Based on the information acquired, it runs a inference scheme that iteratively updates its expectations on the existance of a PU at every candidate location. The following two subsections are the attack models used in [3] and [4] correspondingly. [5] further extends [4]'s attack model by considering the incorporation of the Environment Sensing Capability (ESC) into the SAS, but uses the same inference method. Therefore I'll leave it out in this section.
Attack from [3]:
This paper simplified the communication between the SAS and SUs and considered a TV white space model. As is shown in Figure 4.

Figure 4. Simplified model of data flow.
The attacker is assumed to operate a SU device on the move or several SU devices with fixed locations:

Figure 5. Two equivalent types of adversarial operations. Greens dots denote PUs, red dots denote SUs, devil icons denote SUs operated by the attacker.
The attacker initiates a table of likelihood P of the PU existence of all locations in the grid. After each query-response with the SAS, the attacker's SU gets assigned a channel and a power range to transmit. Based on the power range values, it then updates the likelihoods of all locations regarding to their distance to the attacker's SU. Specifically, if the attacker is assigned a limited transmission power that is lower than the maximum power, all locations with the assigned power range will be safely ruled out and updated with zero likelihood because there are no PUs in it; All locations beyond the assigned power range but within the rannge computed with the maximum transmission power will be updated with higher likelihood, because this ring area must contain one or more PUs which makes the SAS not to assign the full use of maximum transmission power to the SU. Figure 6 illustrates how the update is processed. And this updating procedure keeps going until the likelihood table makes perfect sense and is ready for a decision.

Figure 6. Left: Channel is available but transmission power is limited. Right: Channel is available and maxumum possible transmission power is allowed.
At last, a privacy metric called Incorrectness (IC) is computed directly from these likelihoods P:

With the IC metric at hand, we can then obtain the relation between PU privacy and SU utility through simulation. The simulation results with diffferent privacy protection schemes which will be shown in the next section.
Attack from [4]:
Compared with the previous paper, [4]'s model is more realistic as it considers the interference requirements of the PU, as is shown in the SAS data flow model in Figure 3. Before introducing the attack model, [4] defines an optimization problem for the SAS, that is:
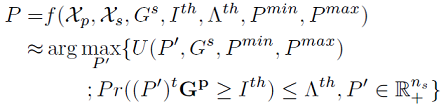
This optimization problem represents the SAS's choice on how to assign the range of transmission power per SU request meanwhile constraining on PUs' interference requirements. This is the key element of the SAS which will be exploited by the adversary for maximum likelihood estimation.
Since we only consider the case that the adversary operates its own SUs, here only presents the second of the three attack models proposed by [4].
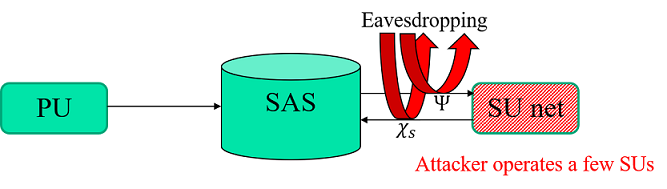
Figure 7. Attack model - compromised SU devices.
In this model, the attacker has access to all communication flows between the SAS and any hacked SU devices, similar to [3]'s model. But unlike [3], this model cannot direct updates the location likelihoods after receiving each SAS response, as it considers a more realistic scenario where it is impossible to derive the likelihood update from the power range because of the interference between each PU-SU pair. Instead it forms a Maximum Likelihood estimation problem with heuristic method.
After a period of time, we assume the adversary has observed T power assignments:

Then based on these observations, the likelihood of the existence of PU for a set of PU candidate locations is:

When the number of total locations N is large (ie. a higher resolution on the area), direct computing the Maximum Likelihood estimation becomes intractable since there are n^2 candidate location sets. Alternatively, heuristic methods are used. After each power assignment, the adversary identifies those locations where a PU could not exist based on her prior knowledge on PU interference criteria. The enimination process keeps going until the number of remain candidate locations is small enough for direct ML calculation. This is called Composite Method. In addition, Interference Constraint Margin (ICM) and Single PU Error (SPE) are used to further lower the computation complexity. In the end, the adversary uses a method called x-sigma to determine the locations with likelihoods x standard deviations beyond the mean likelihood value so that it obtains a small set of locations with very high chance of the existence of a PU.
To measure the efficacy of this inference, this paper uses a metric called Sum Distance Error, which is actually the same meric as the Incorrectness used in [3]. Additionally, PU Privacy Time is used to measure how long the privacy metric can stay above a certain threshold.
Privacy Preserving Techniques and Simulation Results
From the discussion in [3] [4] [5], there are five techniques to enhance PU location privacy:
- 1. False PU entry: A PU sends a set of indistinguishable locations to the SAS instead of its true location.
- 2. Output perturbation with additive noise: The SAS adds negative noise to the assigned power to SUs, which is equivalent to reducing SU's power range and enlarging the PU's protecting contour.
- 3. Putput perturbation with transfiguration: Similar to 3, but the SAS uses a polygon to substitute the protecting coutour rather than a sphere.
- 4. K-anonymity: The SAS groups all PUs into groups of K. All PUs of a single group are non-distinguishable.
- 5. K-clustering: The SAS clusters all PUs into K clusters. All Pus of a single cluster are non-distinguishable.
Interestingly, [3] uses technique 2,3,4,5 while [4] uses 1,2. The reason is that when interference is considered, the notion of "protecting contour" makes no more sense. That's why technique 3,4,5 are hard to implement under the [4]'s settings. The follow two figures show the simulation results from two papers.

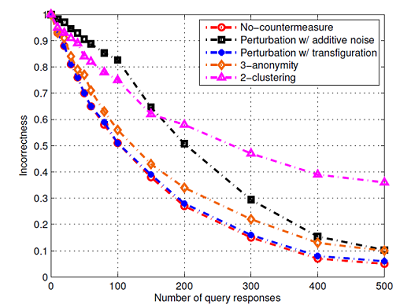
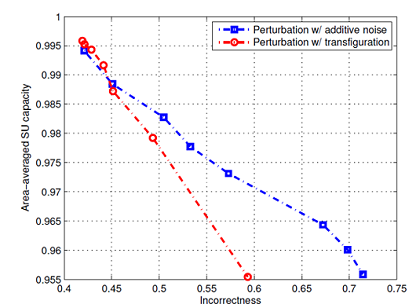
Figure 8. Simulation result from [3]. Left: PU privacu versus number of query-responses under different privacy protection schemes. Perturbation with additive noise works best at first, then 2-clustering overshadows the others when the number of query responses become large. Right: SU utility versus PU privacy under two privacy protection schemes. This shows the fundamental tradeoff between privacy and efficiency. As we see, perturbation with additive noise works better than transfiguration, though the latter is more complicate to implement.

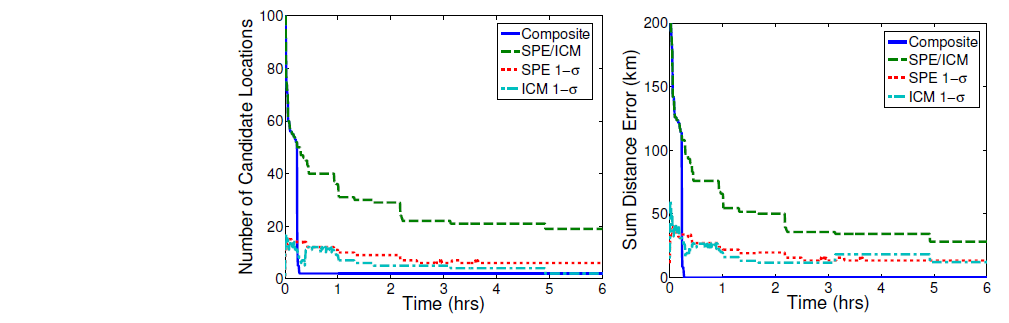
Figure 9. Simulation result from [4]. The SPE identified one PU but totally missed the other. The ICN missed both PUs but with the general areas correct. While the Composite method achieves the best result since it is the only method that spotted out all the 2 PUs, and achieved zero error (zero privacy for PUs) after convergence. Generally, all these heuristic methods achieve good attacking results.
End Notes
In the 3.5 GHz band, the incumbent users were reluctant to share the spectrum from the general public due to security concerns. Indeed, from the simulation results above various PU privacy preserving techniques can only delay the time of breach rather than completely resolving the inference attacks. To the SAS, it always has to make a hard choice between PU privacy and SU utility, which embodies the fundamental tradeoff in this research domain - security versus complexity. However, to strike a balance on this tradeoff depends on the requirements of both sides and it is a viable research option. As time goes on, more of once restrictly frequency band will be available for public use, to which mroe advanced spectrum sharing technologies and privacy preserving techniques will be needed. This is our opportunity.
References
[1] 3.5 GHz Order on Recon and 2nd R&O. FCC 2016. Link [2] 3.5 GHz Band / Citizens Broadband Radio Service. FCC 2015. Link [3] Bahrak, Behnam, et al. "Protecting the primary users' operational privacy in spectrum sharing." DYSPAN 2014. Link [4] Clark, Matthew, and Konstantinos Psounis. "Can the privacy of primary networks in shared spectrum be protected?" INFOCOM 2016. Link [5] Clark, Matthew, and Konstantinos Psounis. "Designing sensor networks to protect primary users in spectrum access systems." WONS 2017. Link [6] Robertson, Andrew, Joseph Molnar, and Jeffrey Boksiner. "Spectrum Database Poisoning for Operational Security in Policy-Based Spectrum Operations." MMILCOM 2013. Link